iOS Basics
Introduction to iOS architecture, security features, and fundamental concepts for understanding the iOS ecosystem.
Based on practical knowledge from Mobile Hacking Lab challenges, this guide covers essential iOS concepts and architecture fundamentals.
Table of Contents
- iOS Architecture Layers
- Core OS Layer
- Core Services Layer
- Media Layer
- Cocoa Touch Layer
- Application Structure
- iOS Inter-Process Communication (IPC)
- iOS Security Features
- References
iOS Architecture Layers
┌─────────────────────────────────────────────────────────────────┐
│ ● ● ● ~ │
├─────────────────────────────────────────────────────────────────┤
│ │
│ Cocoa (Application) │
│ │
├─────────────────────────────────────────────────────────────────┤
│ │
│ Media │
│ │
├─────────────────────────────────────────────────────────────────┤
│ │
│ Core Services │
│ │
├─────────────────────────────────────────────────────────────────┤
│ │
│ Core OS │
│ │
├─────────────────────────────────────────────────────────────────┤
│ │
│ Kernel and Device Drivers │
│ │
│ ┌─────┐ ┌─────────────┐ ┌──────┐ ┌────────────┐ │
│ │ BSD │ │ File System │ │ Mach │ │ Networking │ │
│ └─────┘ └─────────────┘ └──────┘ └────────────┘ │
│ │
└─────────────────────────────────────────────────────────────────┘
Same core OS layer for MacOS, iOS, visionOS, etc...
╔═══════════════════════════════════════════════════════════════╗
║ Application ║
╚═══════════════════════════════════════════════════════════════╝
┃
┃
╔═══════════════════════════════════════════════════════════════╗
║ Cocoa / Cocoa Touch ║
╠═══════════════════════════════════════════════════════════════╣
║ ┌────────┐ ┌─────────┐ ┌───────────┐ ┌────────┐ ║
║ │ UIKit │ │ GameKit │ │ MessageUI │ │ MapKit │ ║
║ └────────┘ └─────────┘ └───────────┘ └────────┘ ║
╚═══════════════════════════════════════════════════════════════╝
┃
╔═══════════════════════════════════════════════════════════════╗
║ Media ║
╠═══════════════════════════════════════════════════════════════╣
║ ┌────────────┐ ┌─────────────┐ ┌─────────┐ ┌─────────┐ ║
║ │ Core Image │ │ Core Audio │ │ OpenGL │ │ OpenAL │ ║
║ └────────────┘ └─────────────┘ └─────────┘ └─────────┘ ║
║ ┌────────────┐ ┌─────────────┐ ┌───────────┐ ┌────────┐ ║
║ │ Core │ │AVFoundation │ │ Core Text │ │ Quartz │ ║
║ │ Animation │ └─────────────┘ └───────────┘ └────────┘ ║
║ └────────────┘ ║
╚═══════════════════════════════════════════════════════════════╝
┃
╔═══════════════════════════════════════════════════════════════╗
║ Core Services ║
╠═══════════════════════════════════════════════════════════════╣
║ ┌────────┐ ┌──────────┐ ┌──────────┐ ┌───────────┐ ║
║ │ SQLite │ │ Core │ │ Core │ │ CFNetwork │ ║
║ └────────┘ │Foundation│ │ Location │ └───────────┘ ║
║ └──────────┘ └──────────┘ ║
║ ┌─────────────┐ ┌────────────┐ ┌───────────┐ ┌────────┐ ║
║ │ Core Motion │ │ Foundation │ │ Core Data │ │ WebKit │ ║
║ └─────────────┘ └────────────┘ └───────────┘ └────────┘ ║
╚═══════════════════════════════════════════════════════════════╝
┃
╔═══════════════════════════════════════════════════════════════╗
║ Core OS ║
╠═══════════════════════════════════════════════════════════════╣
║ ┌─────────────┐ ┌──────────────────────┐ ║
║ │ Kernel API │ │ System Configuration │ ║
║ └─────────────┘ └──────────────────────┘ ║
║ ║
╚═══════════════════════════════════════════════════════════════╝
┃
┃
╔═══════════════════════════════════════════════════════════════╗
║ Hardware ║
╚═══════════════════════════════════════════════════════════════╝
Core OS Layer
Darwin OS
- Foundation for: MacOS, iOS, tvOS, watchOS, visionOS, etc...
'xnu' kernel
- BSD: Unix utilities and networking capabilities.
- Mach: IPC, Memory management.
- Device drivers and I/O kit.
╔═══════════════════════════════════════════════════════════╗
║ Core OS ("Darwin") ║
║ ┌───────────────────────────────────────────────────────┐ ║
║ │ System utilitie │ ║
║ └───────────────────────────────────────────────────────┘ ║
║ ┌───────────────────────────────────────────────────────┐ ║
║ │ Kernel ("xnu") │ ║
║ │ ┌───────────────────────────────────────────────────┐ │ ║
║ │ │ BSD │ │ ║
║ │ │ ┌─────────────────────────────────────────────┐ │ │ ║
║ │ │ │ File systems │ │ │ ║
║ │ │ └─────────────────────────────────────────────┘ │ │ ║
║ │ │ ┌────────────┐ ┌─────────────┐ │ │ ║
║ │ │ │ Networking │ │ NKE │ │ │ ║
║ │ │ └────────────┘ └─────────────┘ │ │ ║
║ │ │ ┌─────────────────────────────────────────────┐ │ │ ║
║ │ │ │ POSIX │ │ │ ║
║ │ │ └─────────────────────────────────────────────┘ │ │ ║
║ │ └───────────────────────────────────────────────────┘ │ ║
║ │ ┌───────────────────────────────────────────────────┐ │ ║
║ │ │ Mach ┌──────────┐ ┌──────────┐ │ │ ║
║ │ │ │ I/O Kit │ │ Drivers │ │ │ ║
║ │ │ └──────────┘ └──────────┘ │ │ ║
║ │ └───────────────────────────────────────────────────┘ │ ║
║ └───────────────────────────────────────────────────────┘ ║
╚═══════════════════════════════════════════════════════════╝
╔═══════════════════════════════════════════════════════════╗
║ Hardware ║
╚═══════════════════════════════════════════════════════════╝
Core Services Layer
Foundation Framework
- Provides basic data types, collections, and other utility classes.
Core Data
- Manages the model layer in the MVC architecture, handling object graphs and persistence.
Core Location
- Provides location-based services using GPS, Wi-Fi, and cellular data.
Networking
- Offers APIs for network communication, including HTTP and Bluetooth.
CloudKit
- Provides cloud storage and data synchronization services.
Media Layer
Core Graphics
- Handles 2D rendering and animations.
Core Animation
- Provides smooth and efficient animations.
AVFoundation
- Manages audio and video playback, recording and processing.
Core Image
- Allows image processing and filters.
Metal and OpenGL ES
- Provides support for high-performance 3D graphics rendering.
Cocoa Touch Layer
UIKit
- Provides the building blocks for constructing the user interface, such as buttons, labels, and table views.
Event Handling
- Manages touch, motion, and remote control events.
Multitasking
- Allows apps to manage background processes and notifications.
Push Notifications
- Handles the reception and processing of remote notifications.
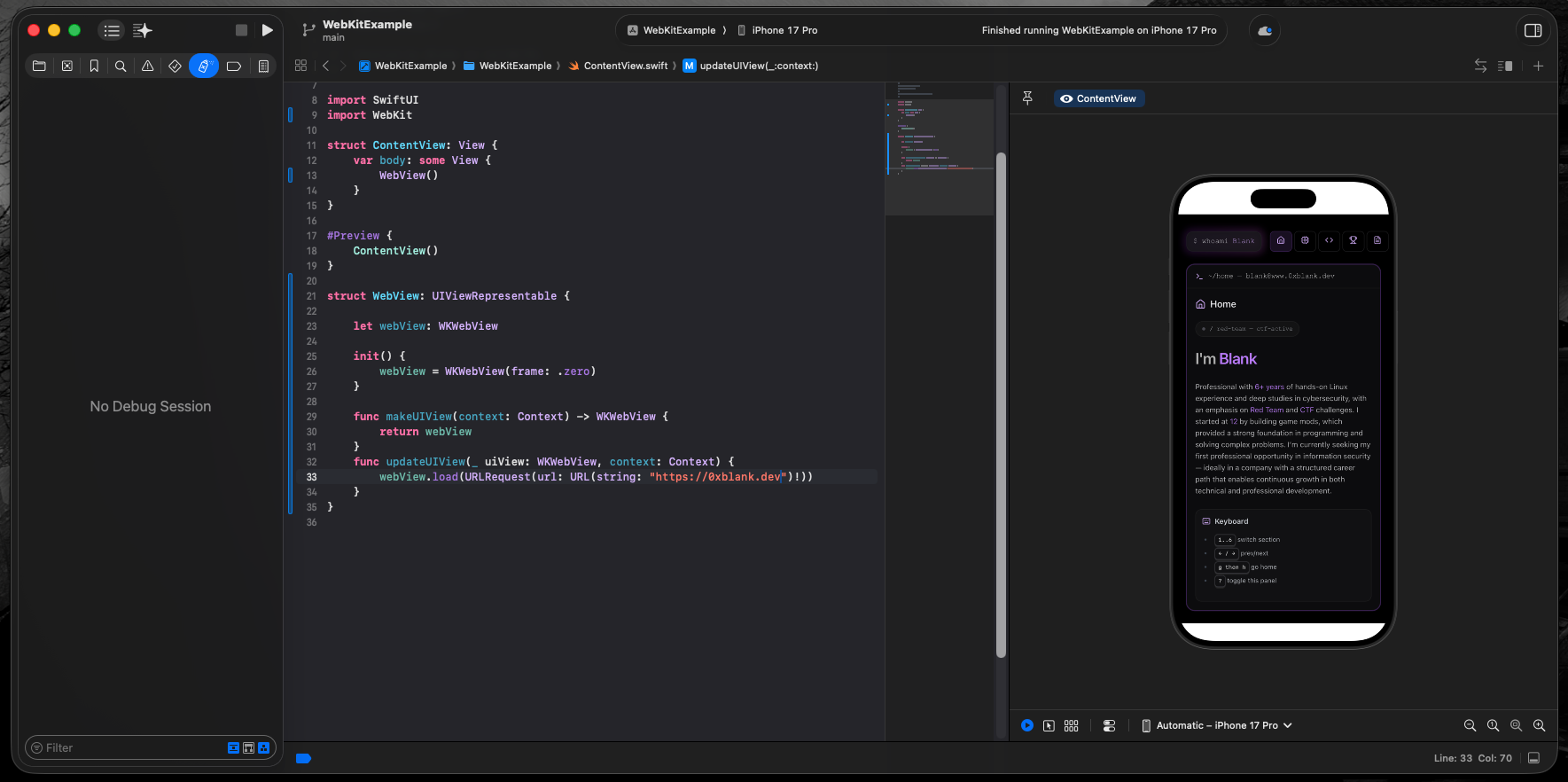
import SwiftUI
import WebKit
struct ContentView: View {
var body: some View {
WebView()
}
}
#Preview {
ContentView()
}
struct WebView: UIViewRepresentable {
let webView: WKWebView
init() {
webView = WKWebView(frame: .zero)
}
func makeUIView(context: Context) -> WKWebView {
return webView
}
func updateUIView(_ uiView: WKWebView, context: Context) {
webView.load(URLRequest(url: URL(string: "https://0xblank.dev")!))
}
}
Application Structure
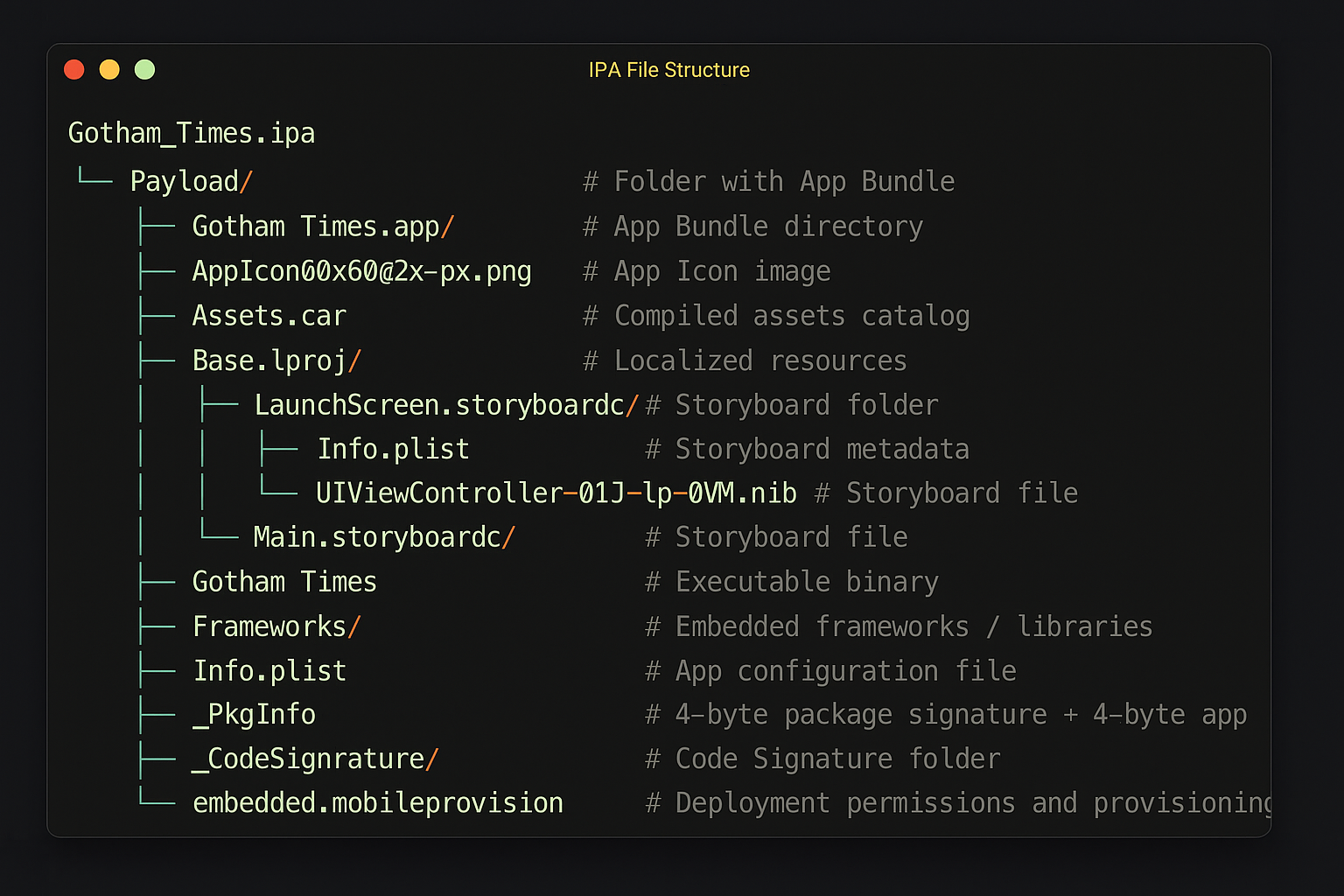
Critical Structure for Security Assessment
Binaries and Code:
Payload/*.app/[AppName]- main executable binary (Mach-O)- *
.dylib- dynamically loaded libraries Frameworks/- private frameworks that may contain vulnerabilitiesPlugIns/- app extensions (widgets, share extensions)
Configuration and Metadata:
Info.plist- permissions, URL schemes, ATS settings, custom protocolsembedded.mobileprovision- provisioning profile, entitlements*.entitlements- capabilities and sandbox exceptionsPkgInfo- package identification
Data Storage:
Documents/- persistent user dataLibrary/Preferences/*.plist- app settings and preferencesLibrary/Caches/- cache that may contain sensitive dataLibrary/Application Support/- app support datatmp/- temporary files (often forgotten)
Resources for Recon:
Assets.car- compiled assets (images, hardcoded strings)*.strings- localization files (may reveal hidden features)*.storyboard / *.nib- compiled interfacesBase.lproj/- base localization resources
Security:
SC_Info/- code signing information_CodeSignature/- code signaturesKeychain(external to bundle, but critical)
Relevant Configuration Files:
*.plist- various configurations*.sqlite, *.db- databases (check encryption)*.json, *.xml- plaintext configurations
Main Attack Vectors:
- Insecure URL schemes in
Info.plist - Sensitive data in
plistsorUserDefaults - Hardcoded certificates/keys in
Assets.car - Unencrypted SQLite databases
- Inadequate backup protection (check NSFileProtection)
- Insecure communication (check ATS bypass)
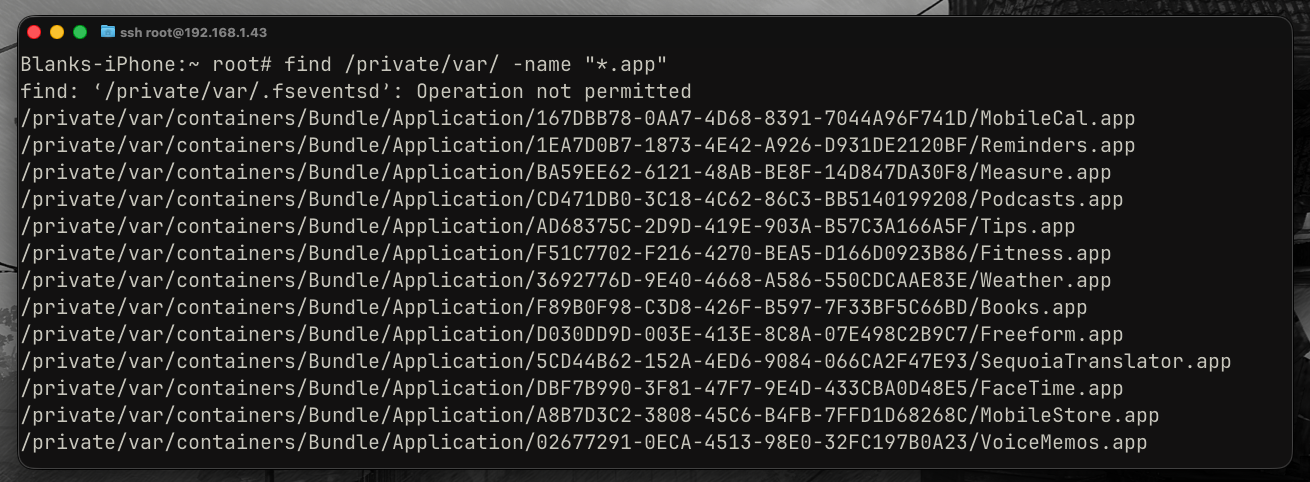
App sandboxes:
find /private/var/containers/Bundle/Application/ -name "*.app"
Main Storyboard or SwiftUI Files
- iOS apps typically use a Main Storyboard (for UIKit-based apps) or SwiftUI files to define user interface.
- These files outline the visual components, layout, and navigation flow of the app.
- The interface is built declaratively, and changes made in these files are reflected in the app's UI.
Frameworks and Libraries
- iOS apps can link against a variety of frameworks and libraries, either provided by Apple (like UIKit, Foundation, Core Data) or third-party libraries.
- These frameworks provide pre-built functionality that developers can use to build apps more efficiently.
Resources and Assets
- The app bundle also contains resources such as images, sounds, localized strings, and other media files.
- These resources are organized in a way that the app can easily access them at runtime.
Entitlements
- Entitlements are permissions that apps can request to access certain system features, such as iCloud, Apple Pay, push notifications, and more.
- These are defined in the app's provisioning profile and Info.plist.
Application Extensions
- iOS apps can provide extensions, which are small, self-contained app components that provide functionality to other parts of iOS or to other apps.
- Examples include Today widgets, Share extensions, and custom keyboards.
Hacky way to create an app
- Build the app in Xcode
- Create an empty directory with the name
Payload - Copy the
.apppackage from the build directory inPayload - Compress the Payload directory in an archive (
.zip) with an app name - Rename the
.zipfile to.ipa - Install the
ipaon a jailbroken device
iOS Inter-Process Communication (IPC)
Several mechanisms for Inter-Process Communication (IPC):
- URL Schemes
- Pasteboard
- App Groups and Shared Containers
- XPC Service
URL Schemes
- Apps can open other apps or send data by specifying a custom URL scheme.
Pasteboard
- A shared clipboard that allows apps to share small bits of data like text or images.
App Groups and Shared Containers
- Allow apps from the same developer to share files and data securely.
XPC Services
- Lightweight services that allow apps to communicate with separate processes.
iOS Security Features
Hardware Security
Secure Enclave
Cryptography
- The Secure Enclave generates and manages encryption keys that are isolated from the rest of the system, ensuring that the keys remain secure (even if the main processor is compromised).
Biometric Data Protection
- Biometric data (fingerprint and facial recognition data) is encrypted and stored only within the Secure Enclave.
- It is never accessible to the operating system or applications.
Hardware Root of Trust
Boot ROM
- This is the first code executed when an iOS device is powered on.
- It is immutable and built into the hardware, verifying the next stages of the boot process.
Chain of Trust
- Each stage of the boot process is cryptographically signed and verified by the previous stage, ensuring that only authenticated and unaltered code is executed.
Device Encryption
File Encryption
- Each file is encrypted with a unique key, which is tied to the user's passcode and the device's UID.
Data Protection Classes
- iOS uses different levels of protection depending on the type of data and its importance, such as ensuring that certain files are only accessible when the device is unlocked.
App Sandbox
Isolated Environment
- Each app runs in its own sandboxed environment, limiting its interactions with other apps and the operating system.
Resource Access
- Apps must request permission to access resources like the camera, microphone, location data, or contacts, which is managed by iOS's privacy controls.
Code Signing and Integrity
Developer Certificates
- All iOS apps must be signed with a valid Apple-issued certificate.
- This prevents unauthorized code from running on the device.
Runtime Integrity
- iOS continually verifies the code signature of running applications, protecting against code injection or modification.
Secure Boot Chain
Boot Loader Verification
- The boot loader, responsible for loading the kernel, is cryptographically verified by the Boot ROM.
Kernel Integrity
- The iOS kernel is signed and verified before it is allowed to execute, preventing unauthorized modifications.
Privacy Features
App Permissions
- Users are prompted to grant or deny access to sensitive information, such as location, photos, and contacts, on a per-app basis.
Transparency
- Apps must disclose why they need access to certain data, and users can view and manage permissions through iOS settings.
Tracking Prevention
App Tracking Transparency (ATT)
- Apps must ask for permission before tracking users across apps and websites.
Privacy Reports
- iOS provides reports to users showing which apps have accessed sensitive information or attempted to track them.
Secure Communication
HTTPS Everywhere
- iOS encourages the use of HTTPS for secure web communication, with apps required to support it by default.
VPN and Wi-Fi Security
- iOS supports VPNs and secure Wi-Fi connections, protecting data as it travels over potentially insecure networks.
Wi-Fi Security Features
- Auto-Join Security: iOS devices will not automatically connect to untrusted Wi-Fi networks.
- MAC Address Randomization: When scanning for networks, iOS devices use randomized MAC addresses, preventing tracking of devices based on their MAC address.
General Exploit Mitigations
Address Space Layout Randomization (ASLR)
- Randomizes memory addresses used by the system and app processes to prevent attackers from predicting target locations in memory, making it harder to execute certain types of attacks, such as buffer overflows.
Data Execution Prevention (DEP)
- Ensures that certain areas of memory are marked as non-executable, preventing malicious code from being executed from those locations.
Pointer Authentication Codes (PAC)
- PAC adds cryptographic signatures to pointers in memory, making it difficult for attackers to manipulate them without detection.
Stack Canaries
- A security feature that places a small random value (canary) before the stack return pointer.
- If the canary is altered, the app can detect the buffer overflow and prevent exploitation.
System Integrity Protection (SIP)
- Limits the capabilities of the root user to protect system integrity, reducing the attack surface available to malware and attackers.
App Store and Updates
App Store Review Process
App Review
- All apps submitted to the App Store undergo a review process to check for malicious behavior, adherence to guidelines, and privacy standards.
Developer Accountability
- Developers are held accountable for their apps behavior, and Apple can remove apps that violate policies or pose security risks.
Patch Management
- Apple regularly releases security updates that are easily deployable to users, ensuring that devices remain protected against the latest threats.
Forced Updates
- For critical vulnerabilities, Apple can enforce updates to ensure all users are protected.
Jailbreaking Mitigations
System Integrity Protection (SIP)
- iOS includes measures that make it difficult to jailbreak the device without introducing significant vulnerabilities.
- Sometimes referred to as "rootless".
Frequent Updates
- Apple regularly updates iOS to patch vulnerabilities that could be exploited by jailbreaks.
References
Mobile Hacking Lab:
- https://www.mobilehackinglab.com/
- https://www.mobilehackinglab.com/course/free-ios-application-security-course
Apple Documentation: